Secure and Manage Access with HashiCorp Boundary
Secure and Manage Access with HashiCorp Boundary
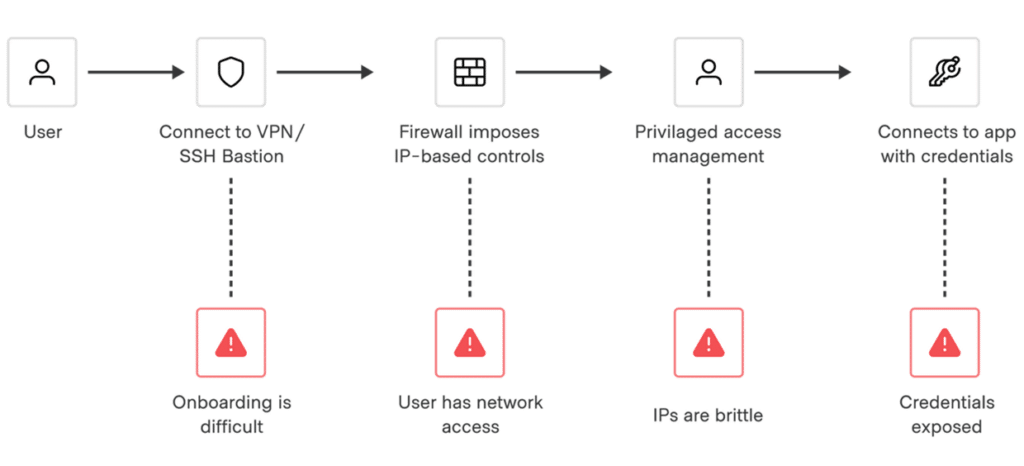
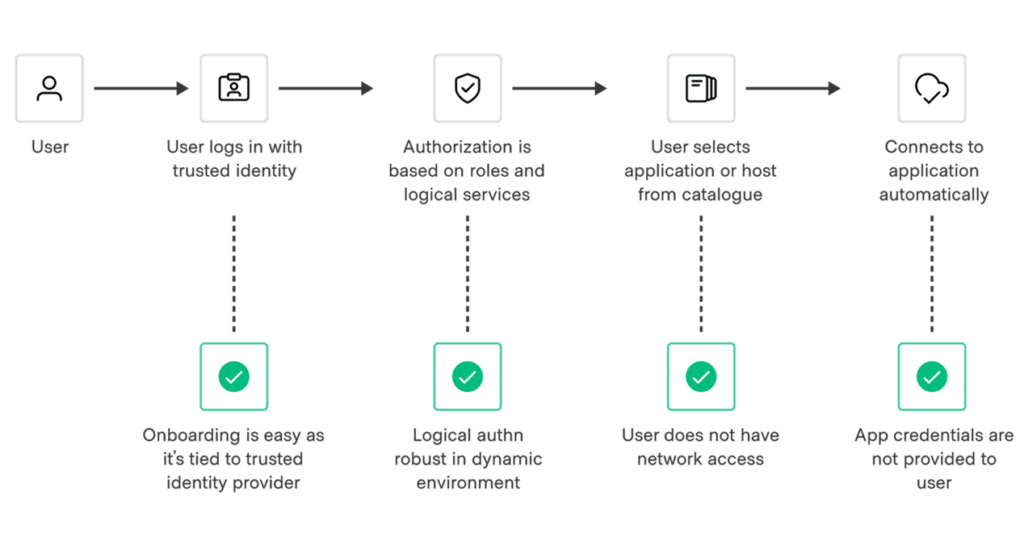
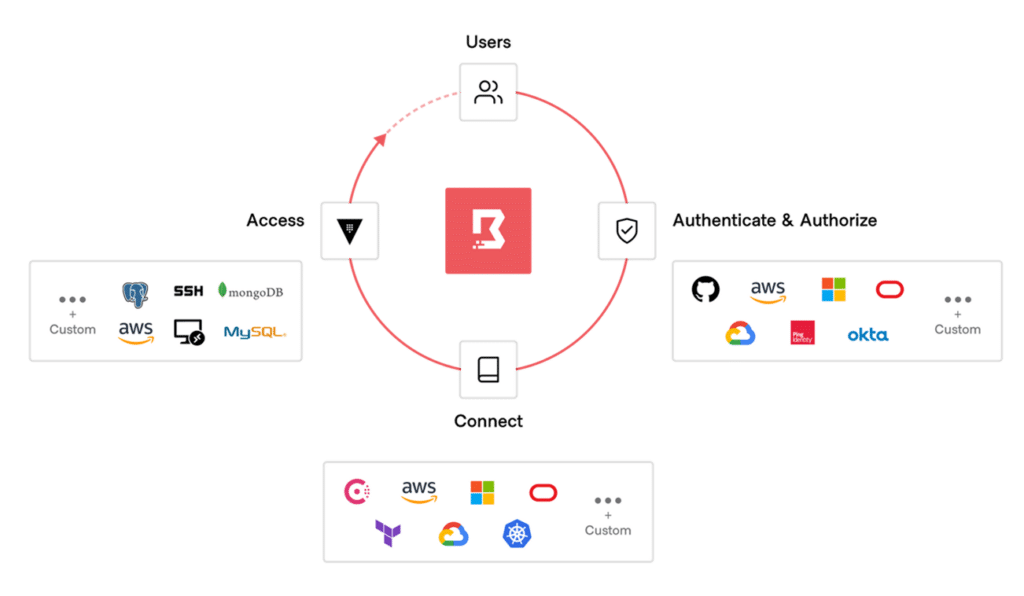
HashiCorp Boundary provides a modern solution for managing human-to-machine access, reducing risks associated with credential sprawl and manual maintenance efforts required by traditional solutions like SSH keys and VPN credentials.