In my previous blogs, I talked about the various ways to install the Carbon Black sensor and how this works in a non-persistent VDI environment. So now have secured our virtual infrastructure, what to do with all the physical devices like corporate laptops and desktops? Or maybe you have a BYOD policy within your company, but still want to offer more security for you and your employees?
In this blog, I will explain how to install the Carbon Black sensor on mobile devices, whether they are domain-joined or not, that are managed by VMware Workspace ONE.
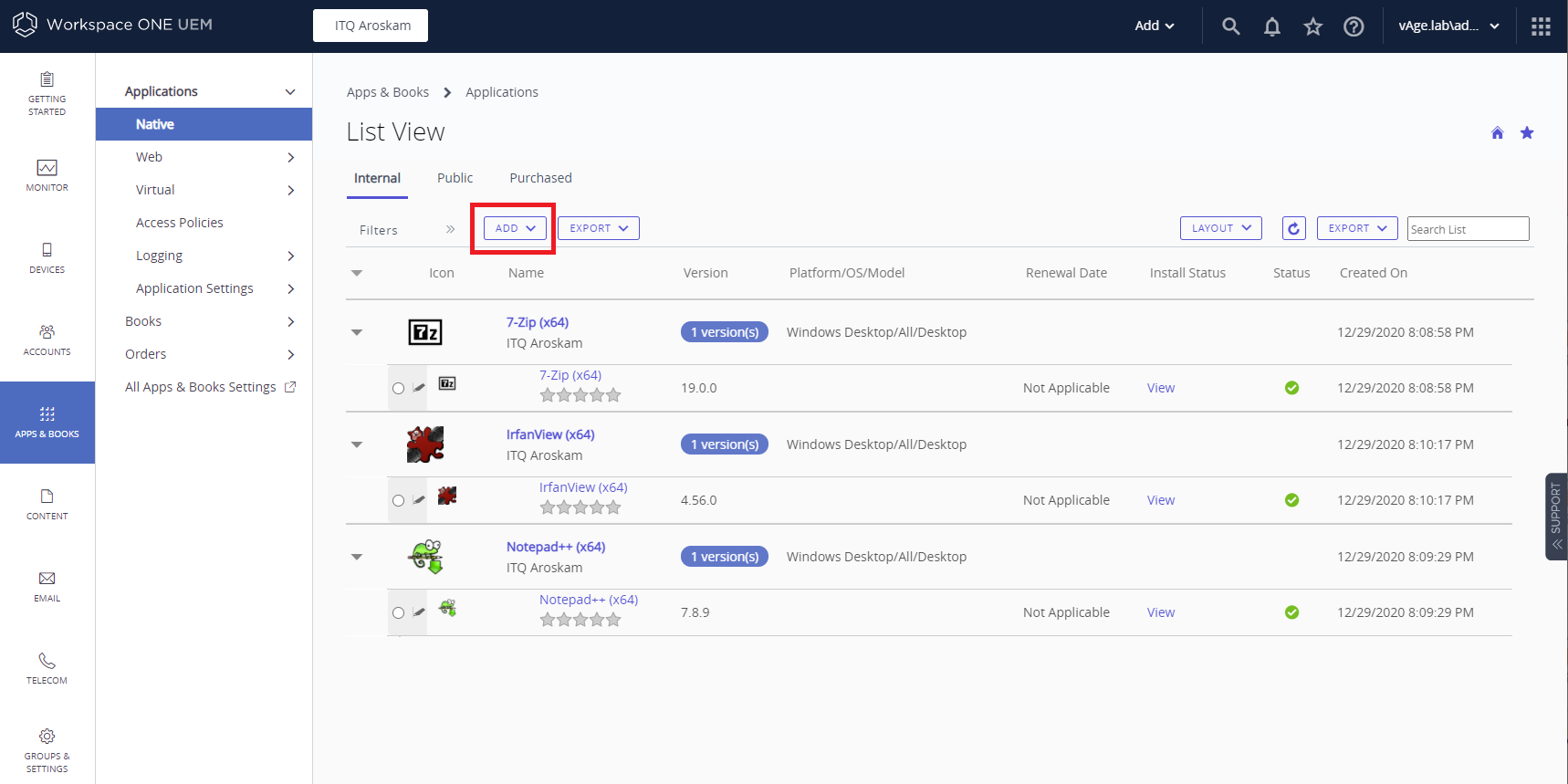
To install the Carbon Black sensor, you obviously need to have access to VMware Workspace ONE UEM. Log in to the management page and go to APPS & BOOKS > Native and click on the Add > Application File.
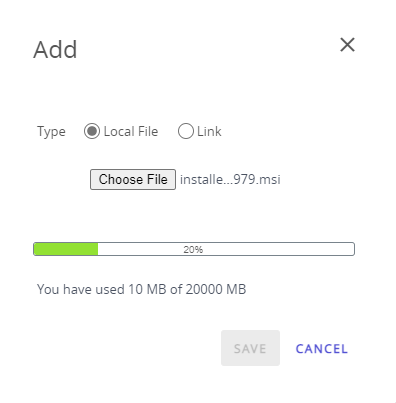
Click on the Upload > Choose file and select the Carbon Black MSI installer. If you haven’t downloaded the installer yet, you can download it from the Carbon Black Cloud management page. Click Save to upload the file.
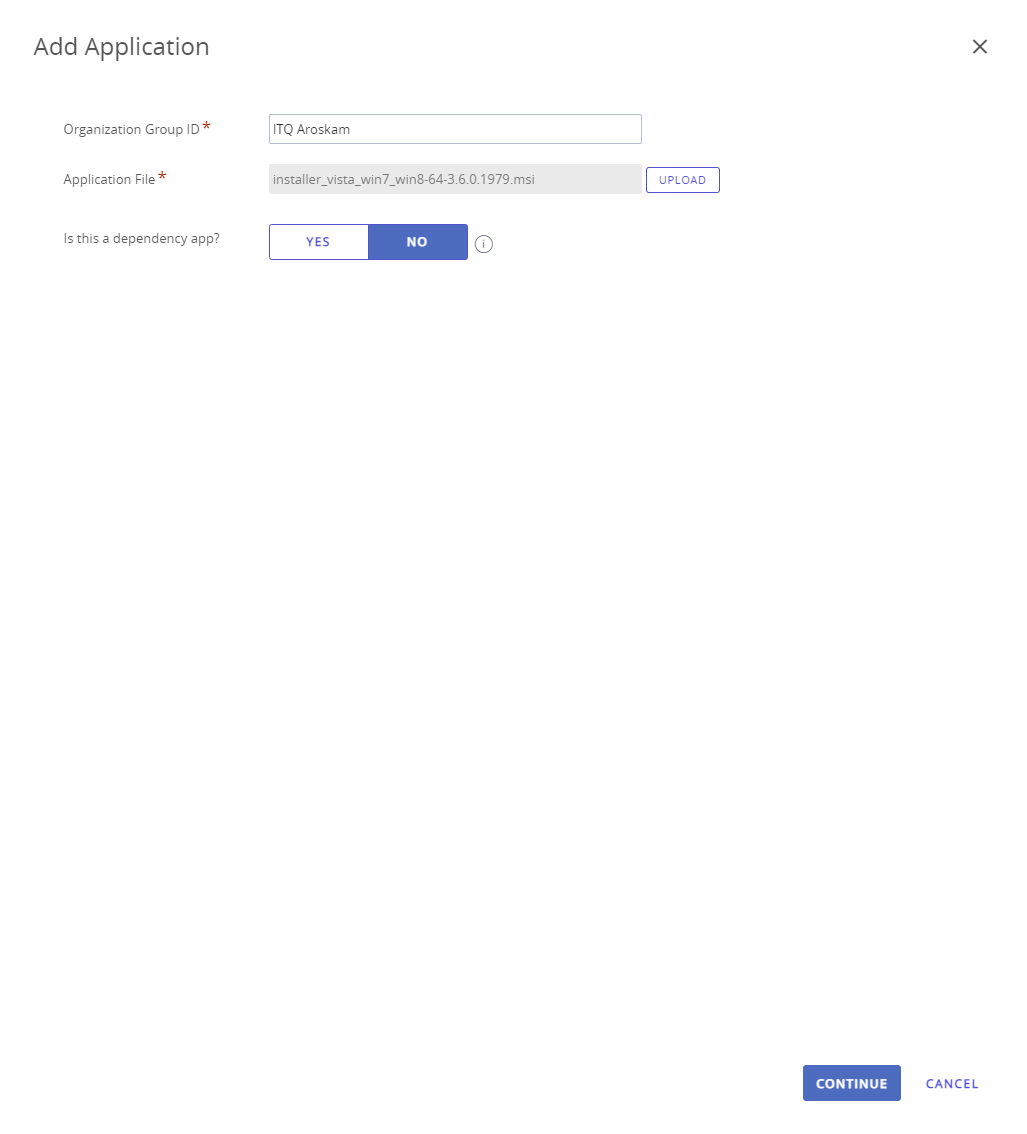
After a minute the upload will be ready. The sensor is not a dependency app, so leave it at NO and click Continue.
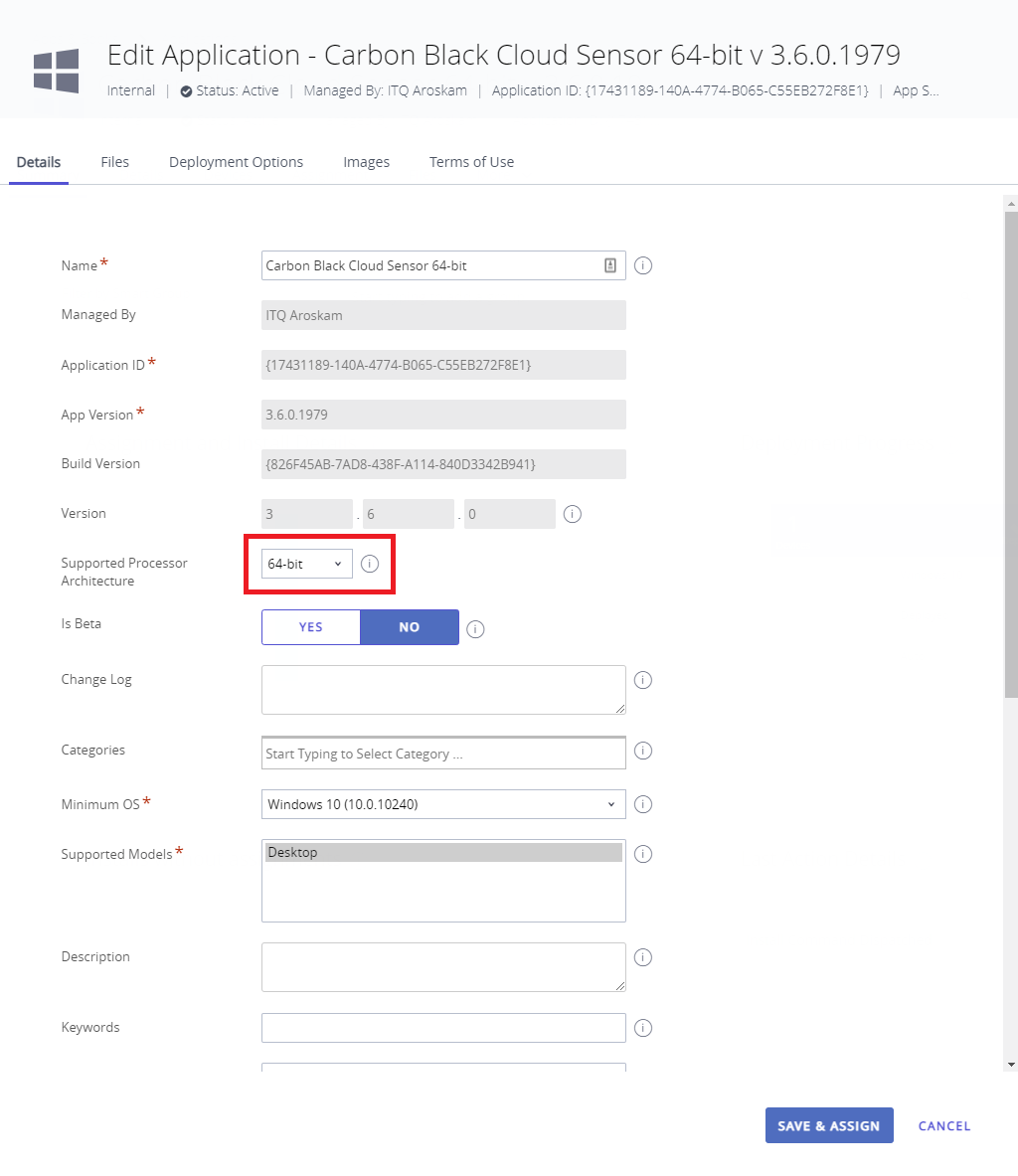
Workspace ONE UEM will now analyze the installer and come up with an application overview on how they think the application should be installed. 99% of the time you need to adjust a couple of settings to get the application correctly installed. First of all, check the Supported Processor Architecture. This is set at 32-bit by default. Of course, we are installing the sensor on Windows 10 64-bit, so change it to 64-bit.
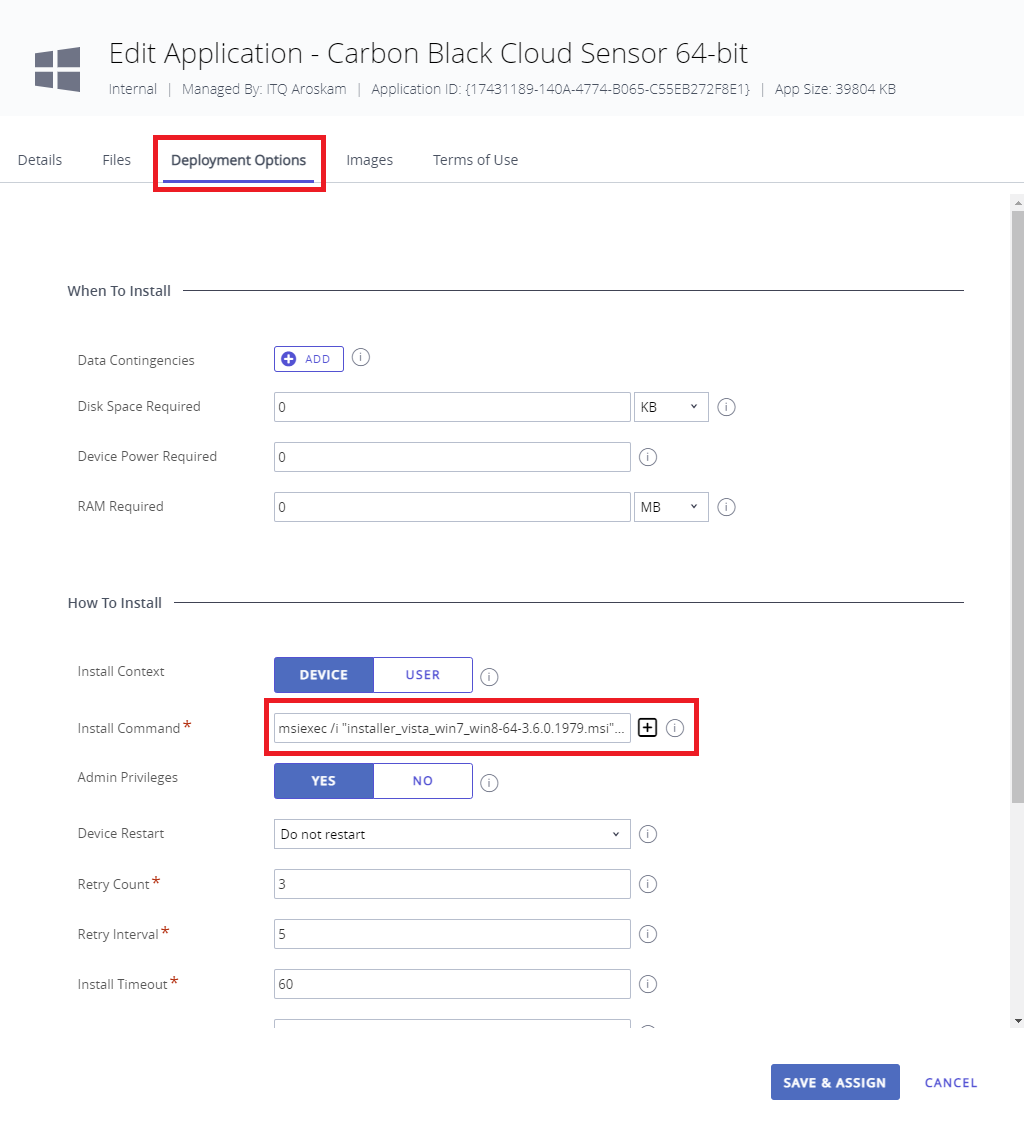
When you click on the Deployment Options tab, you will see that the Install Command is already filled. We need to change this because if we leave this default the sensor does not know what Carbon Black Cloud to talk to, so we need to add the COMPANY_CODE parameter to the command line.
The command line should look like this:
msiexec /i “installer_vista_win7_win8-64-3.6.0.1979.msi” /qn COMPANY_CODE=”7PRI————#E8″
After you entered the correct command line, click Save & Assign.
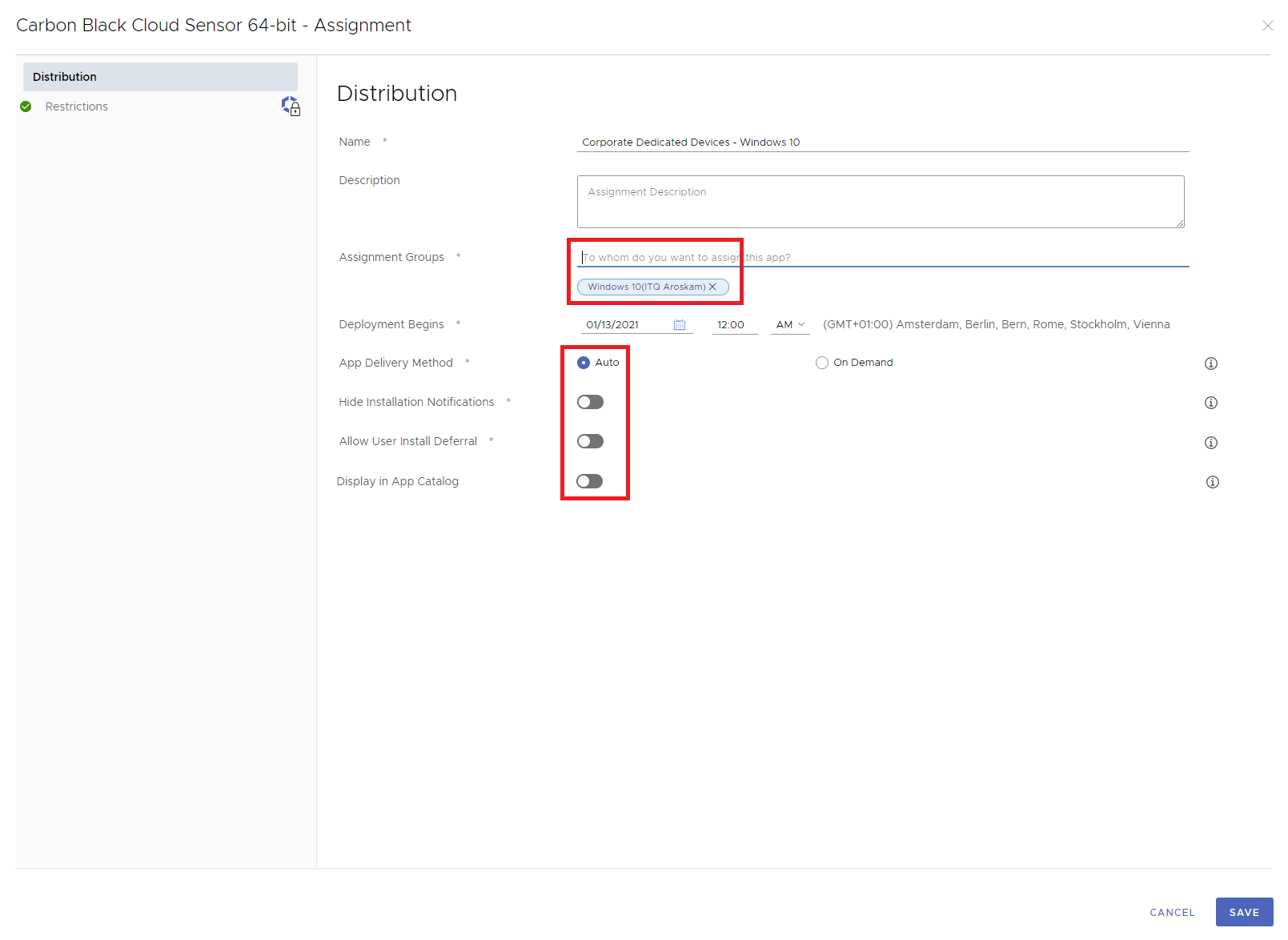
You have various options to assign an application. In my case, I have created a Windows 10 assignment group which I use to deploy applications to Windows 10 devices.
For the App Delivery Method, I selected Auto to force the application to be installed automatically. I also disabled Notifications, allow user install deferral, and the application will not be shown in the App Catalog.
You can set these options as you like, click Save to continue.
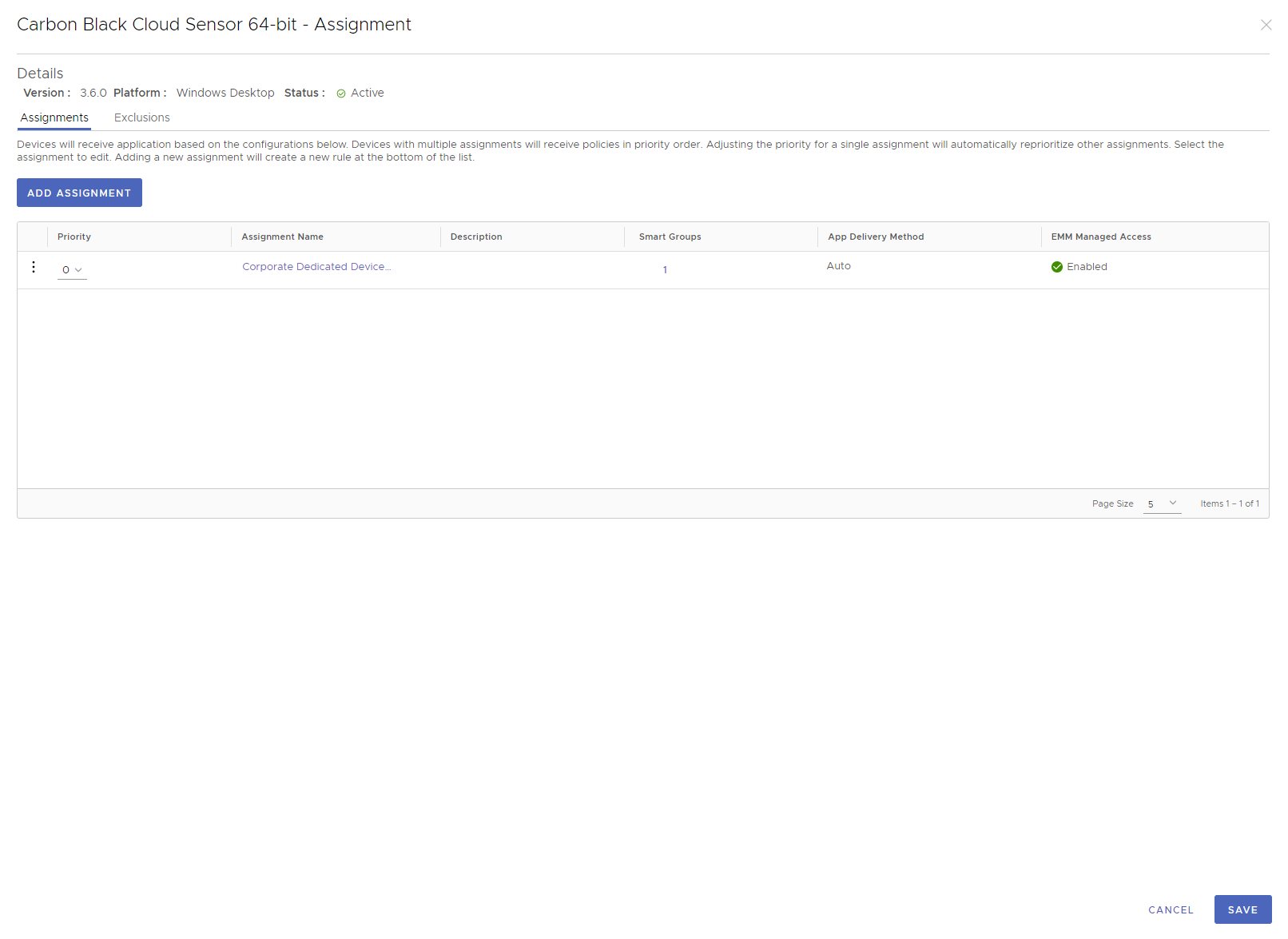
Click Save to continue.
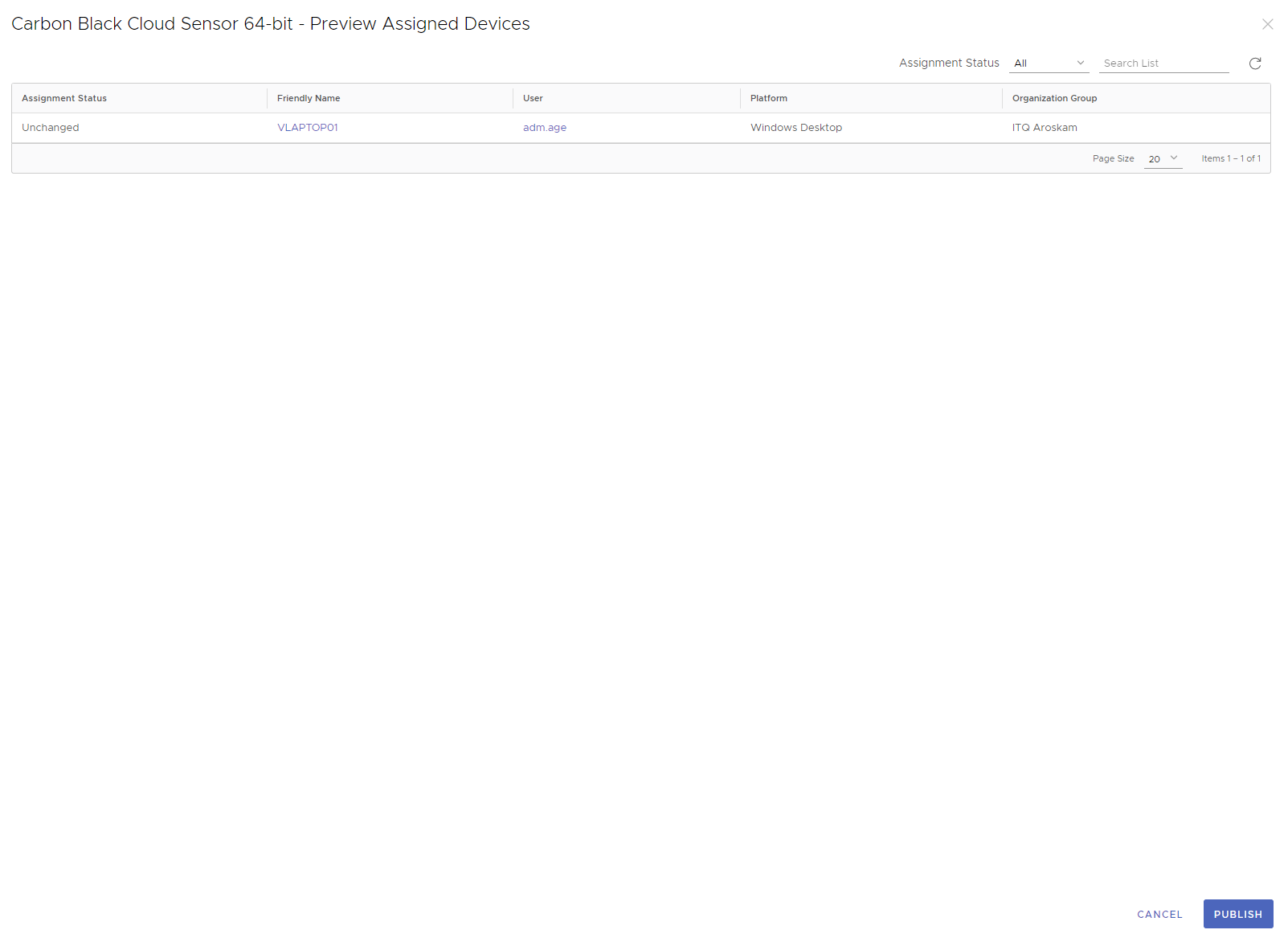
Click Publish to finish the creation of the native app in Workspace ONE UEM.
Now that we are ready, the application will immediately be pushed to all devices in the assignment group. Because we disabled all notifications and visibility in the App Catalog, the Carbon Black sensor is silently installed on the device.
There are a couple of ways to check if the installation was successful and the sensor is up and running.
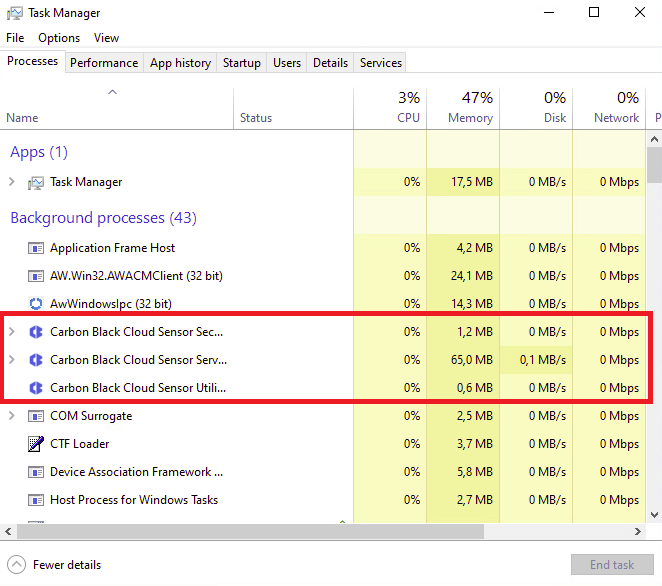
You can open the task manager on the device, and check if the Carbon Black processes are running.
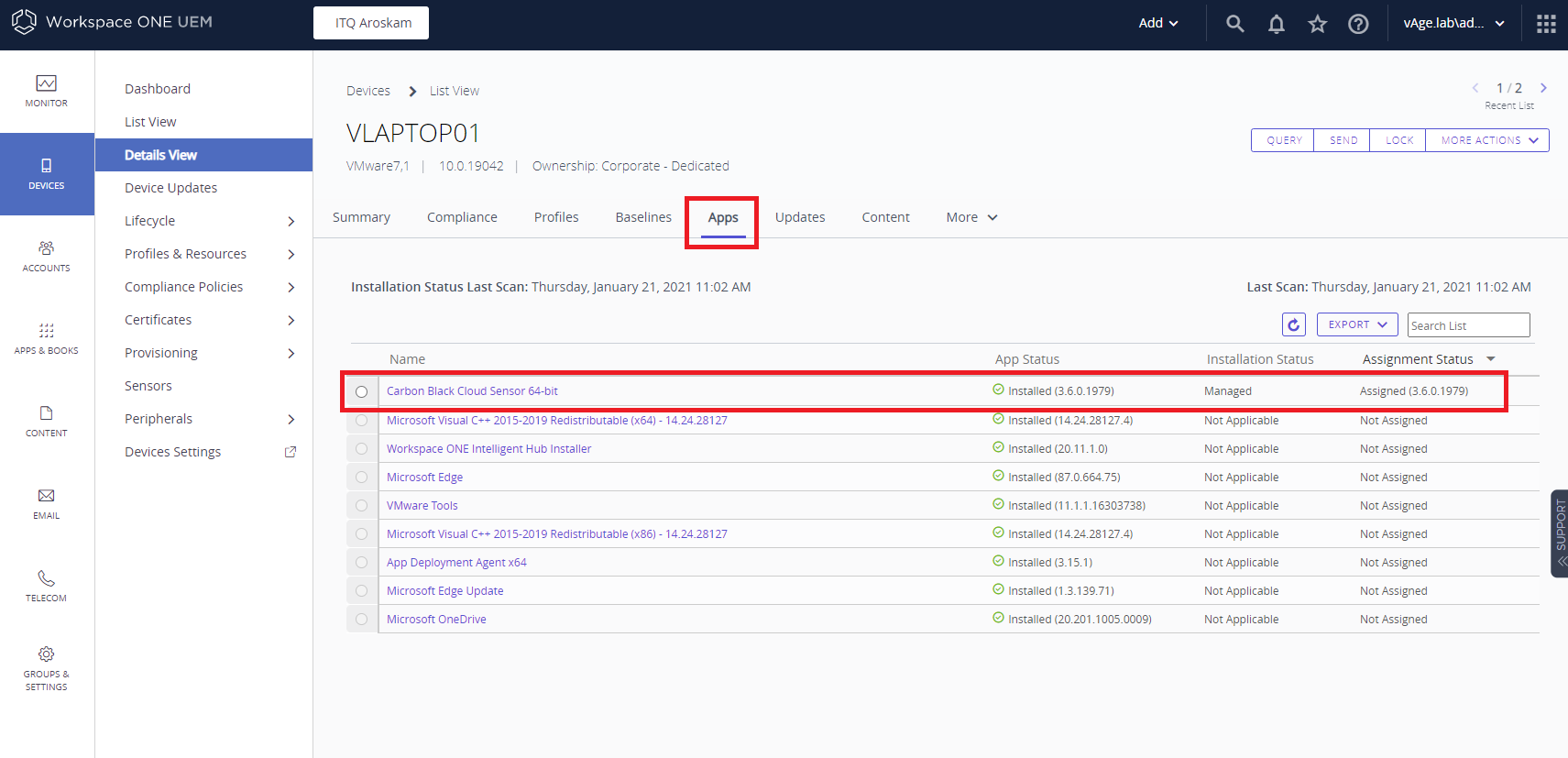
You can also check the Workspace ONE UEM console. Click Devices > Select a device and click on the Apps tab.
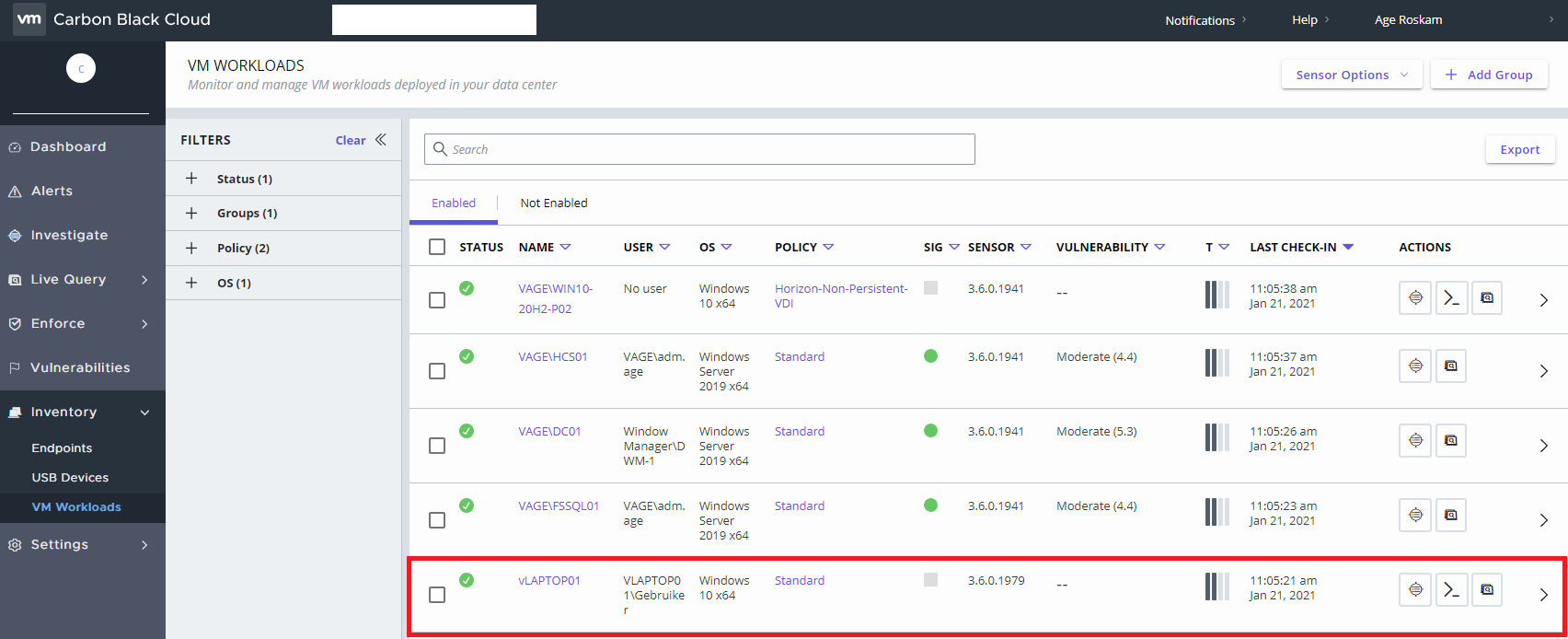
And of course, you can check if the device is shown on the Carbon Black Cloud management page. Open the management page and go to Inventory > Endpoints (in this example I used a virtual “laptop”, so I’m checking the VM Workloads page)
Conclusion
As you can see the installation of the Carbon Black sensors through VMware Workspace ONE UEM is also really straightforward. The ease of deploying the sensors in all various ways makes Carbon Black a joy to use. If you are interested in a demo, feel free to contact me, or keep an eye out for more on Carbon Black and Workspace ONE Intelligence!
Het bericht Securing devices with VMware Carbon Black and Workspace ONE UEM verscheen voor het eerst op Age Roskam.
The original article was posted on: ageroskam.nl