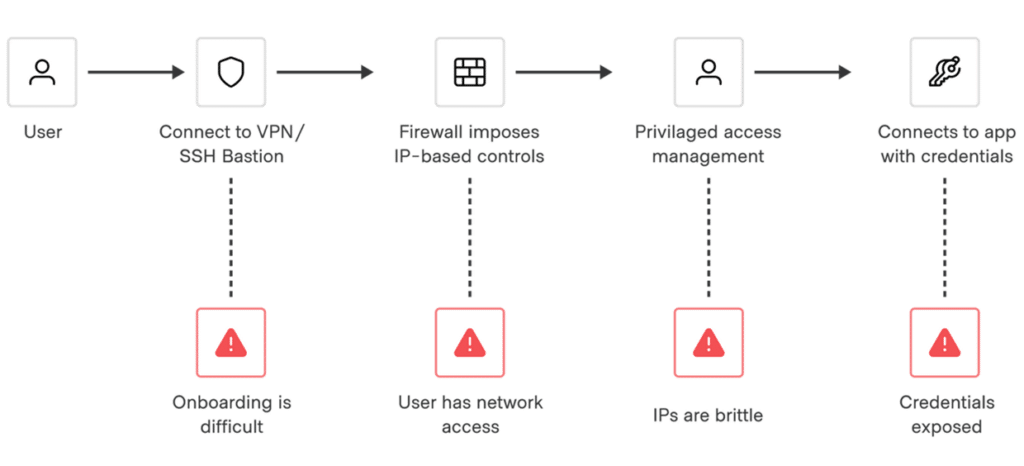
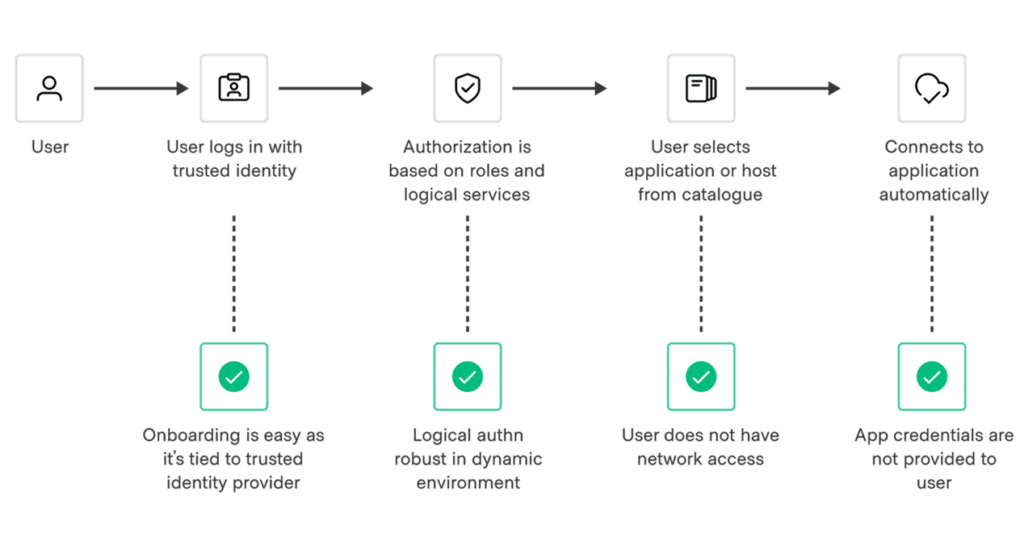
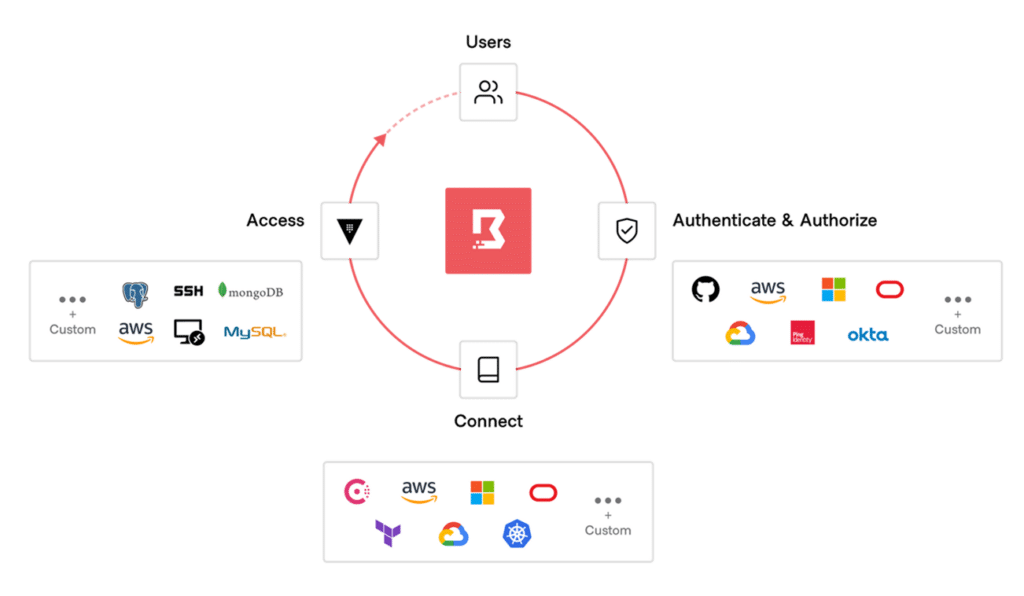
Platform engineers can streamline just-in-time access to privileged sessions for users and applications. Teams can control access permissions with extensible role-based access controls.
Platform teams can define the perimeter of resources, identities, and access controls as code through Boundary's fully instrumented Terraform provider, REST API, CLI, and SDK. They can automate the discovery of new resources and enforcement of existing policies as resources are provisioned.
Security engineers can monitor and manage each privileged session established with Boundary. Session logs can be exported to a wide variety of analytics tools.
 Secure and Manage Access with HashiCorp Boundary
Secure and Manage Access with HashiCorp Boundary