This blog post describes the steps for creating a custom connector in VMware Workspace ONE Intelligence that can send messages to your Microsoft Teams channel(s).
Use Case
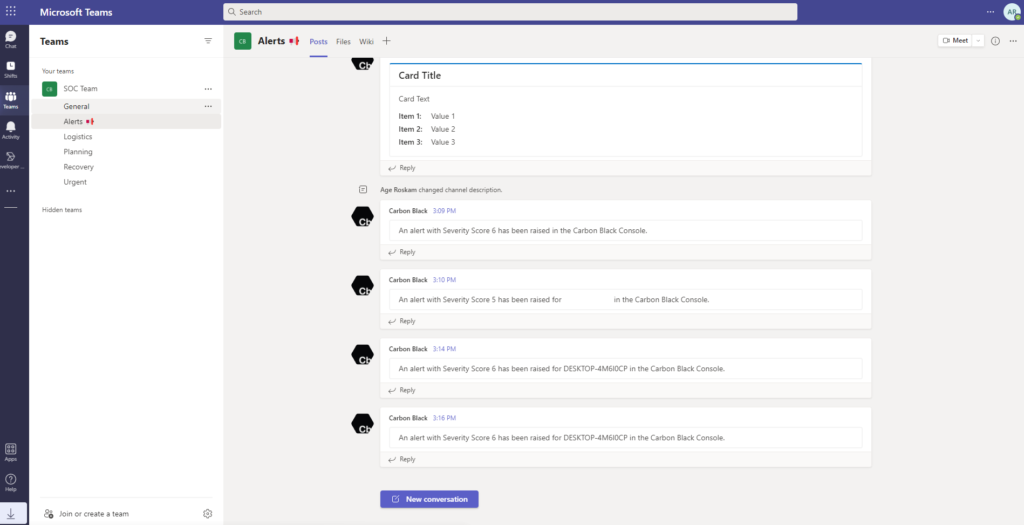
In my Microsoft 365 Developer environment, I have created a new Team and some additional channels to simulate a SOC team. In the alerts channel, I want Workspace ONE Intelligence to post any new Carbon Black alerts with a severity of 6 or higher.
Requirements
If you want to follow along, you need to have a Workspace ONE Intelligence tenant, a Microsoft Office 365 subscription with Teams, and Postman to create and modify the API. I’m using my VMware TestDrive environment and a Microsoft 365 Developer account for this in my lab environment.
Microsoft Teams
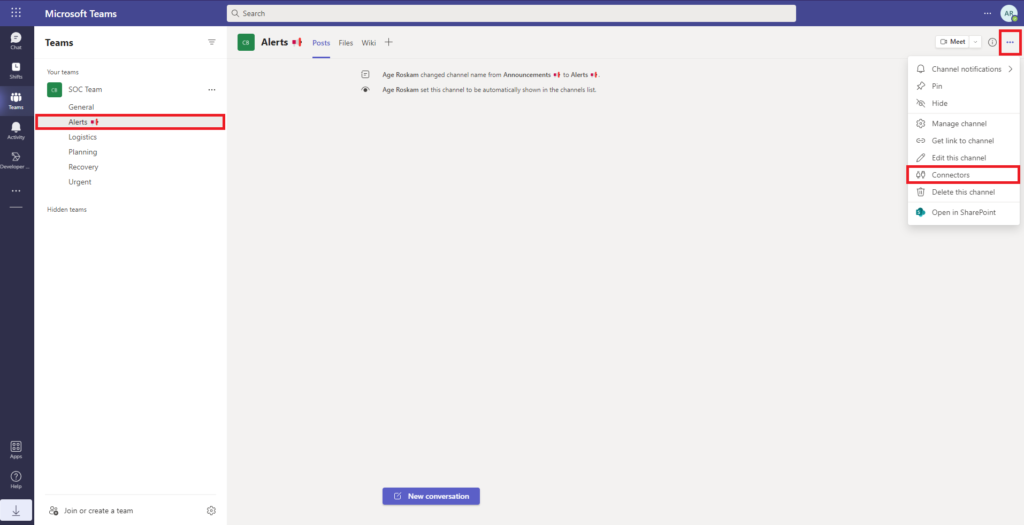
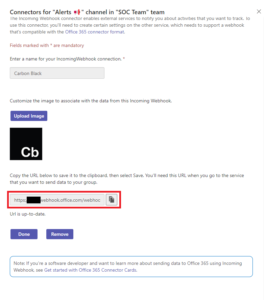
As said, I’ve created an Alerts channel for Workspace ONE Intelligence to post any new alerts found in Carbon Black. Select the channel, on the top right click on the … (dots) and select Connectors.
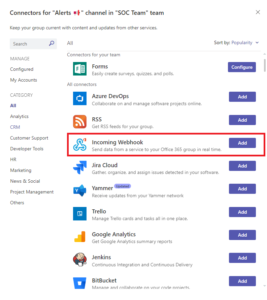
Search for Incomming Webhook and select Add.
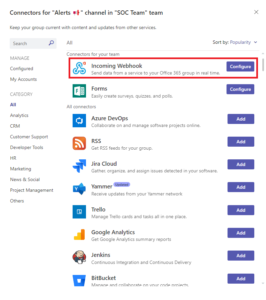
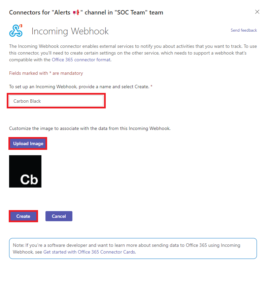
Select Configure, give the connector a Name, and optionally Upload an image.
Copy & save the webhook URL in a notepad for later use, and click Done.
Postman
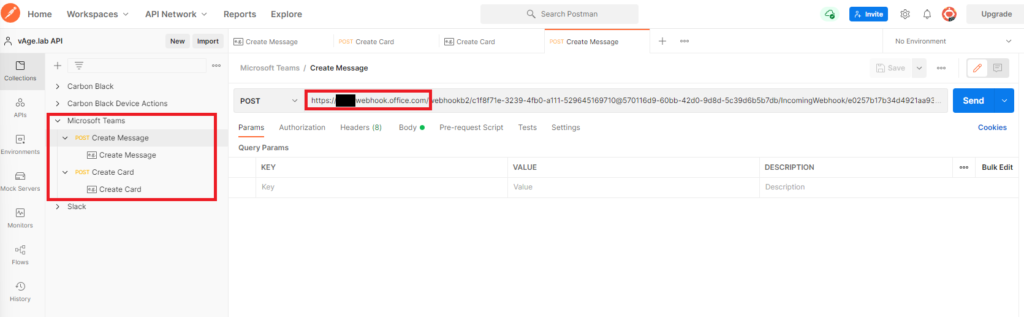
Luckily you don’t have to create your own API. You can download the Microsoft Teams JSON file from the EUC samples page on Github. Click here.
Import the JSON file into Postman. Insert the webhook URL in each of the POST requests.
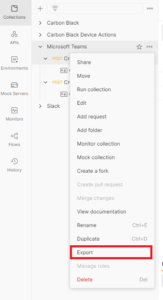
Click on the … (dots) at the Microsoft Teams level and select Export.
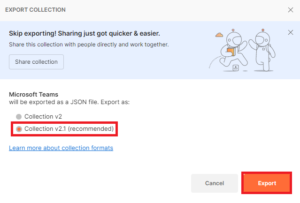
Leave it on the default Collection v2.1, click on the Export button and save the JSON file on your computer.
Workspace ONE Intelligence
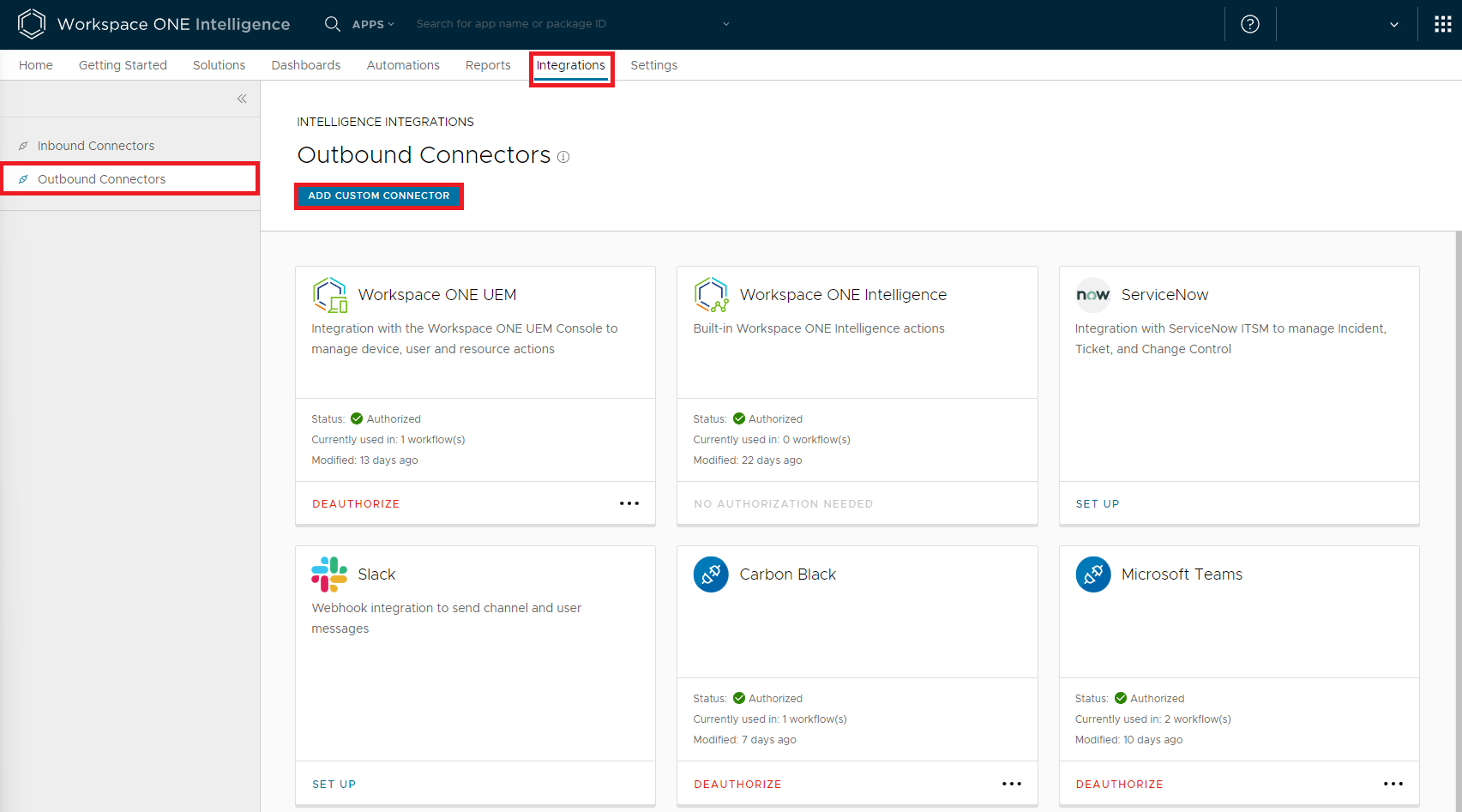
Open a browser and go to your Workspace ONE Intelligence tenant, select Integrations > Outbound Connectors > Add Custom Connector.
Copy the webhook URL into the Base URL field, and select No Authentication in the Auth Type field. Click Save to add the connector.
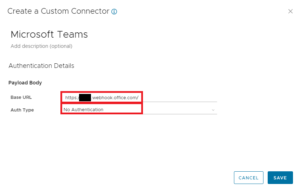
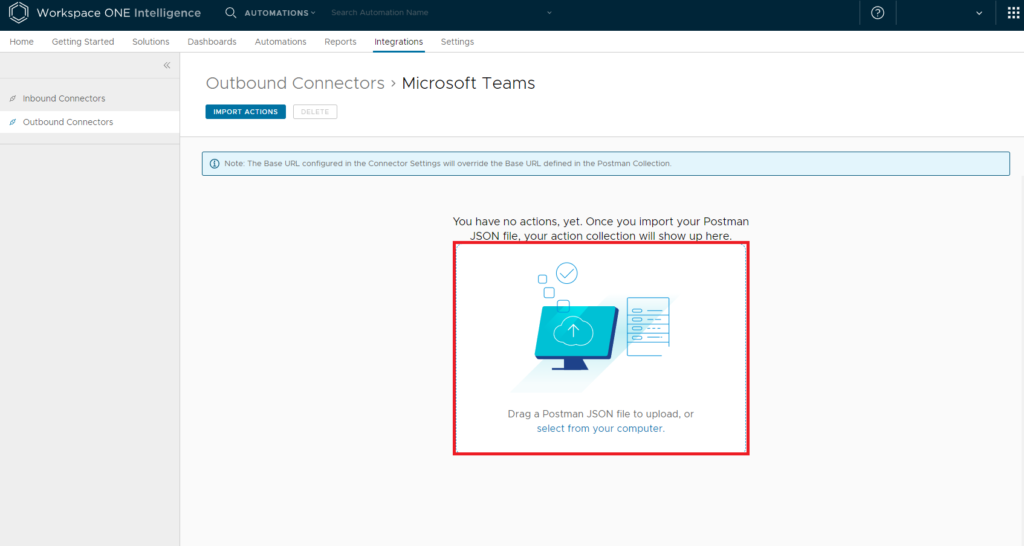
Click on the … (dots) of the Microsoft Teams connector and select View Actions. Drag the created JSON file to the upload field to import the Microsoft Teams API.
If all went well, you should see two new imported actions, and you are ready to use them in any automation you want.
The test
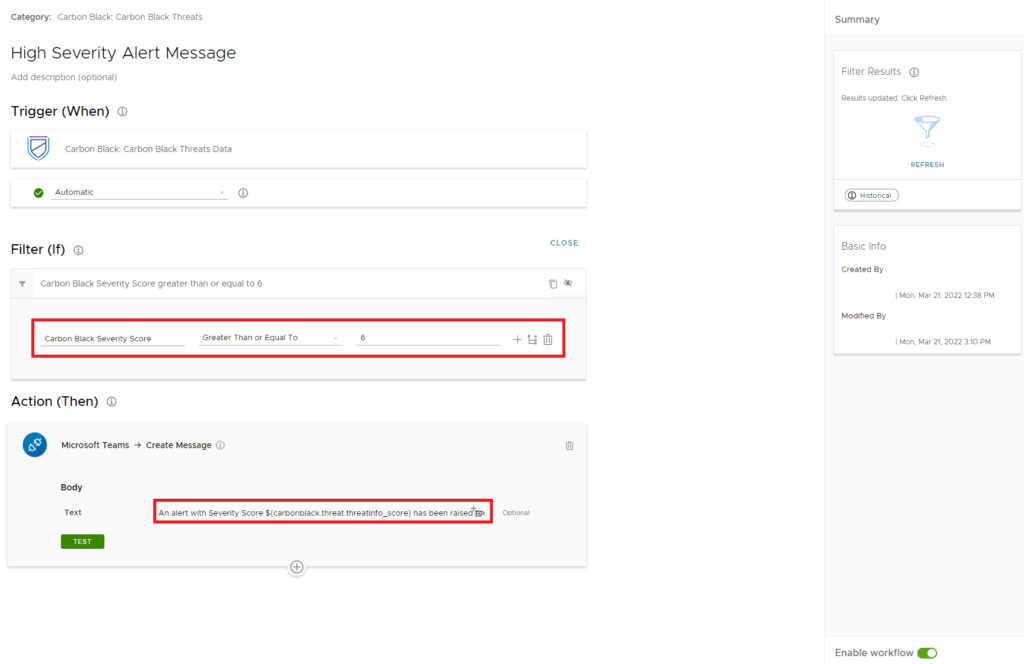
As said, I want to get an alert in my teams channel if Workspace ONE Intelligent monitors any type of Carbon Black alert with a severity higher than 6. To set this up, I’ve created the following Automation in Workspace ONE Intelligence.
*Before you can do this, you need to have Carbon Black integrated with Workspace ONE Intelligence.
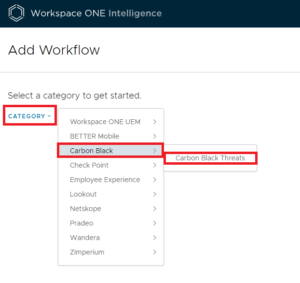
In Workspace ONE Intelligence go to Automations > Add > Custom Workflow. Then select Category > Carbon Black > Carbon Black Threats.
In the Filter (IF) field, select Carbon Black Severity Score > Greater Than or Equal To > 6.
In the Action (Then) field, enter a message you want to send to the teams channel. I used the following message:
An alert with Severity Score ${carbonblack.threat.threatinfo_score} has been raised for ${carbonblack.threat.deviceinfo_devicename} in the Carbon Black Console.
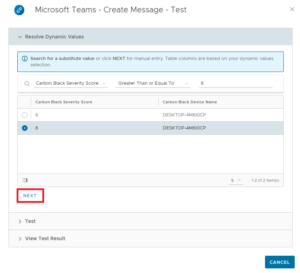
Then click the Test button to start the test.
In the new window, select one of the alerts found and click Next. (If you don’t see any alerts change the filter to a lower severity)
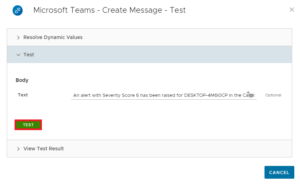
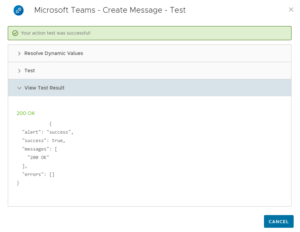
The text in the text field should automatically be adjusted, click Test to launch send the message to Microsoft Teams.
If you see 200 OK your message has successfully been send to your teams channels.
Open your teams channel and see the result!
I hope this has been informative. If you have any questions or comments, let me know.
Het bericht Create a custom connector for Microsoft Teams in Workspace ONE Intelligence verscheen voor het eerst op Age Roskam.
The original article was posted on: ageroskam.nl